Invoking AWS CodeBuild from Jenkins
This page describes the required configuration for Jenkins to invoke AWS CodeBuild, which in turn invokes Synopsys Detect.
The procedure described here references the AWS CodeBuild project that was created and verified in the Calling Synopsys Detect from AWS CodeBuild page.
The procedure described here references the AWS CodeBuild project that was created and verified in the Calling Synopsys Detect from AWS CodeBuild page.
- Set up Jenkins. If you already have a Jenkins server set up to use the AWS CodeBuild plugin, go to Step 2 (If not, you can do either step).
- Download Jenkins at jenkins.io and run it directly with java -jar jenkins.war.
- Create a Jenkins server on Amazon EC2 in the AWS Marketplace.
- Download and install the AWS CodeBuild plugin.
The AWS CodeBuild plugin enables Jenkins to launch AWS CodeBuild.
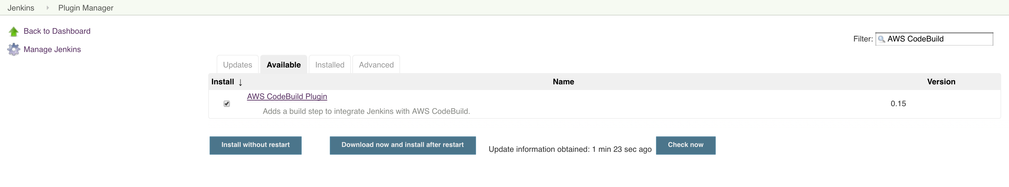
There are two methods (a or b) that you can use to download and install the AWS CodeBuild plugin:- Download and Install AWS CodeBuild Plugin by using the Plugin Manager, which is the recommended option.
- In Jenkins, click Manage Jenkins > Manage Plugins > Available.
- In the Filter text box, type AWS CodeBuild.
- Select the AWS CodeBuild plugin.
- Click Download now and install after restart.
- Restart Jenkins.
- Download the AWS CodeBuild plugin manually.
- Build the AWS CodeBuild Jenkins plugin locally by running mvn install to generate aws-codebuild.hpi in the target directory,
or
Download the latest aws-codebuild.hpi from the Jenkins plugin repository. - In Jenkins, click Manage Jenkins > Manage Plugins > Advanced > Upload Plugin > Browse to find and select the aws-codebuild.hpi file > Upload to install the AWS CodeBuild plugin.
- Build the AWS CodeBuild Jenkins plugin locally by running mvn install to generate aws-codebuild.hpi in the target directory,
- Download and Install AWS CodeBuild Plugin by using the Plugin Manager, which is the recommended option.
- Configure Jenkins Environment Variables.
- Configure the AWS Access Key ID and Secret Access Key in the Jenkins Environment variables area.
Click here to see information about creating and obtaining the access and secret access key IDs for an IAM user. - In Jenkins, click Manage Jenkins > Configure System > Global Properties > Environment Variables > Add > Save.
- Configure the AWS Access Key ID and Secret Access Key in the Jenkins Environment variables area.
- Invoke the AWS CodeBuild plugin in Jenkins by using either of the following methods described in steps a. and b.
- Use the AWS CodeBuild plugin with the Jenkins Pipeline plugin.
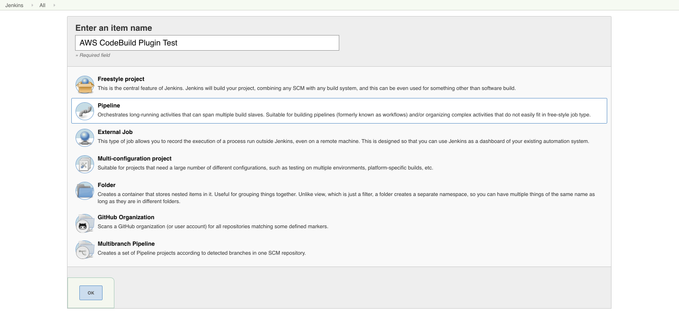
- To create the Pipeline job, type an item name in the Enter an item name text box, select Pipeline, and then click OK.
- Invoke the AWS CodeBuild plugin by using a pipeline script.
Click the created pipeline job > Configure > Pipeline.
This invokes the AWS CodeBuild through a pipeline script. The following script is a sample script:
The AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY are retrieved from the Jenkins environment variables that were configured in Step 3.node { stage('Build') { // Invoke the AWS CodeBuild awsCodeBuild artifactLocationOverride: '', artifactNameOverride: '', artifactNamespaceOverride: '', artifactPackagingOverride: '', artifactPathOverride: '', artifactTypeOverride: '', awsAccessKey: env.AWS_ACCESS_KEY_ID, awsSecretKey: env.AWS_SECRET_ACCESS_KEY, buildSpecFile: '', buildTimeoutOverride: '', credentialsId: '', credentialsType: 'keys', envVariables: '', projectName: '<project name>', proxyHost: '', proxyPort: '', region: 'us-east-1', sourceVersion: '', sseAlgorithm: '' } }- Build the Pipeline job.
- To create the Pipeline job, type an item name in the Enter an item name text box, select Pipeline, and then click OK.
- Use the AWS CodeBuild plugin with the Jenkins build step.
- To create a Freestyle job type an item name in the Enter an item name text box; select Freestyle project, and then click OK.
- To invoke the AWS CodeBuild plugin by using a Jenkins build step, click the created freestyle job > Configure > Build > Add build step > Select AWS CodeBuild.
- Click AWS Configuration > Manually specify access and secret keys > Add your AWS Access Key and AWSSecret Key.
- Configure the region, project name, and source; either Use Project source or Use Jenkins source.
- Provide other properties as appropriate.
- Click Save.
- Build the freestyle job.
- To create a Freestyle job type an item name in the Enter an item name text box; select Freestyle project, and then click OK.
- Use the AWS CodeBuild plugin with the Jenkins Pipeline plugin.
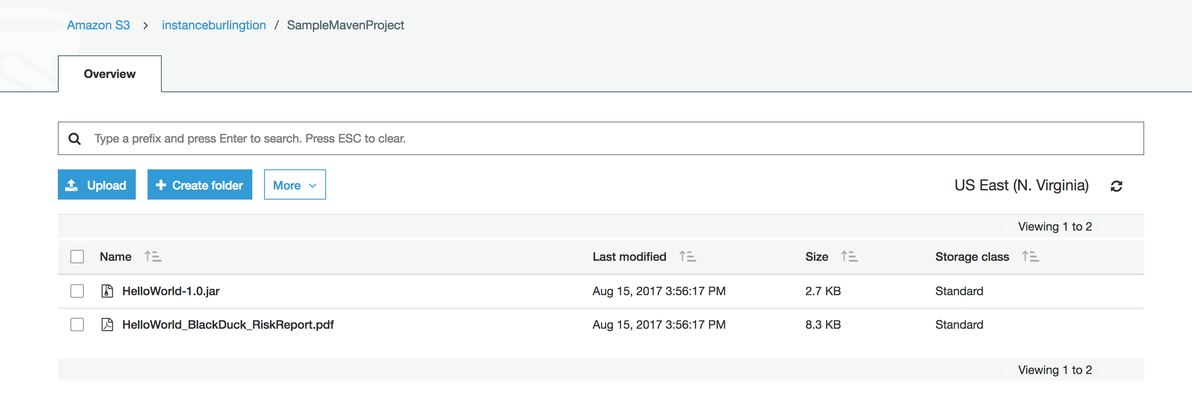
- Download and view the artifacts from S3 following a successful build.
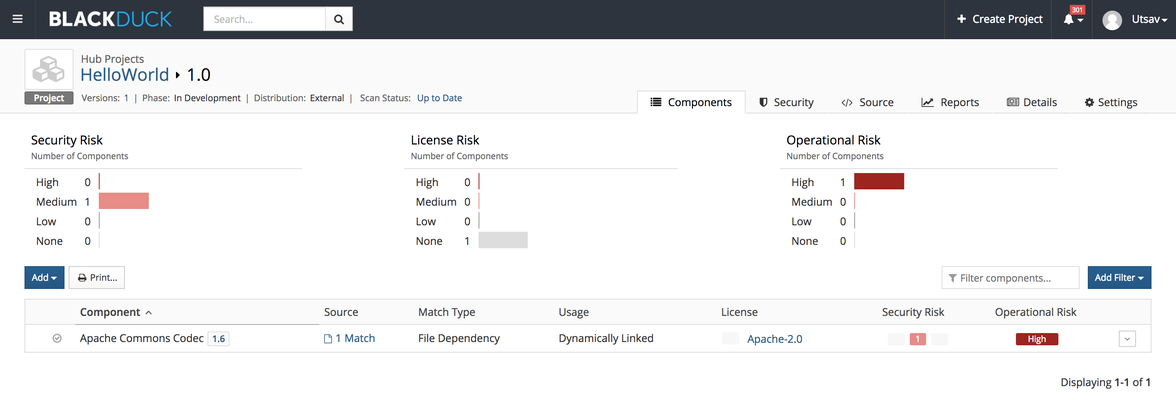
The artifacts are pushed to S3. As part of the artifact, it contains the built artifact and the risk profile report in PDF file format. - View more details about the scan results in your Black Duck Hub instance.
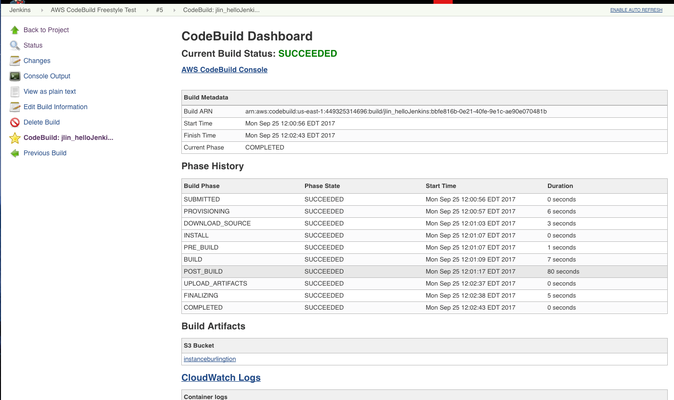
- To view the console logs in Jenkins,
click the created pipeline or freestyle job > finished build job # > CodeBuild: <project name> to view the CodeBuild Dashboard.
©2020 Synopsys, Inc. All Rights Reserved