Calling Synopsys Detect from AWS CodeBuild
Table of Contents
Introduction
You can use Synopsys Detect to scan any application that is built on AWS CodeBuild and is invoked in the build spec.
The build spec is a collection of build commands and related settings, in YAML format that CodeBuild uses to run a build.
You can either, include a build spec as part of the source code or define the build spec when you create a build project.
For more information about how build spec works, refer to How CodeBuild Works.
A Maven project is used as an example in the following procedure:
Before You Begin
For best results, before you scan with Coverity on Polaris (Coverity only, or Coverity with Black Duck), create a Coverity YAML configuration file.
Also, Synopsys recommends that you add your Synopsys credentials in the AWS Parameter Store.
Invoking Synopsys Detect
Create a buildspec.yml file in the root directory of the source code to be built with AWS CodeBuild.
If you created a CodeStar project, the buildspec.yml file already exists in your project’s root directory.
The buildspec.yml specification describes two phases for the Synopsys Detect invocation:- Phase 1
Installing the latest Synopsys Detect shell script from GitHub and making it executable, which is described in the install stanza. - Phase 2
Executing Synopsys Detect.- For Coverity scanning with or without Black Duck; this is described in the build stanza.
For Black Duck scanning only; this is described in the post_build stanza.
The installation specification is the same, whether you are scanning Coverity or Black Duck.
The invocation/execution of Synopsys Detect varies based on the type of scanning.
Click examples to learn how to construct a buildspec.yml file, whether you are calling Coverity on Polaris, Black Duck, or both.
- Phase 1
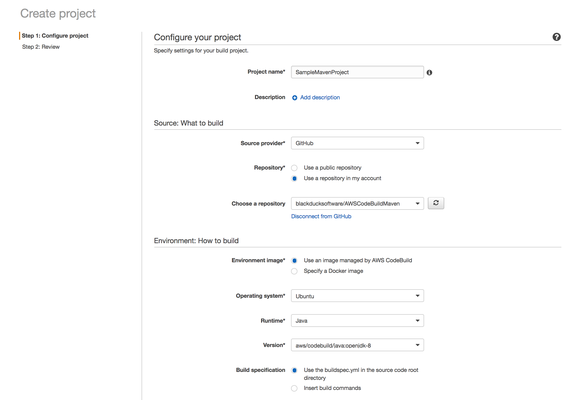
- Create the AWS CodeBuild project.
Ensure that you use the same region that is used to store the Parameter Store values.- Navigate to Services > Developer Tools > CodeBuild > Create Project.
- Type the project name and description.
- Select the source provider.
- Select the repository where your source code is located.
- Select the image, operating system, runtime, and the runtime version.
- Select the artifact type and bucket name. If the bucket is unavailable, create the bucket.
- Select Create a service role in your account if you don't already have one.
Service Roles can be re-used across CodeBuild projects. - Click Continue and Save.
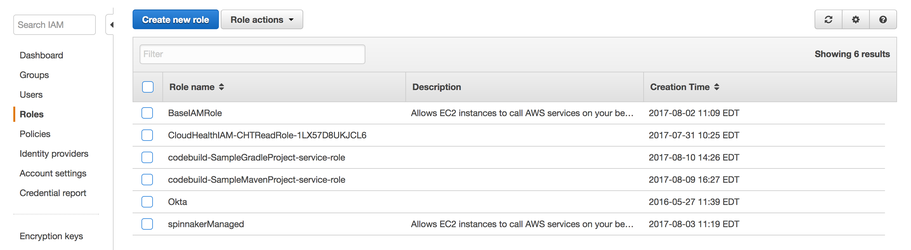
- Attach the policy that was created in Adding Synopsys Credentials to the AWS Parameter Store to the CodeBuild Worker Role.
- Navigate to Services > Security, Identity & Compliances > IAM > Roles.
- Find the service role associated with the CodeBuild project:
- If a new role was created with a default name in Step 3, it has the following syntax:
- codebuild-<project_name>-service-role
- If you use CodeStar, the role is already created and has the following syntax:
- CodeStarWorker-<project_name>-ToolChain
- CodeStarWorker-<project_name>-ToolChain
- If a new role was created with a default name in Step 3, it has the following syntax:
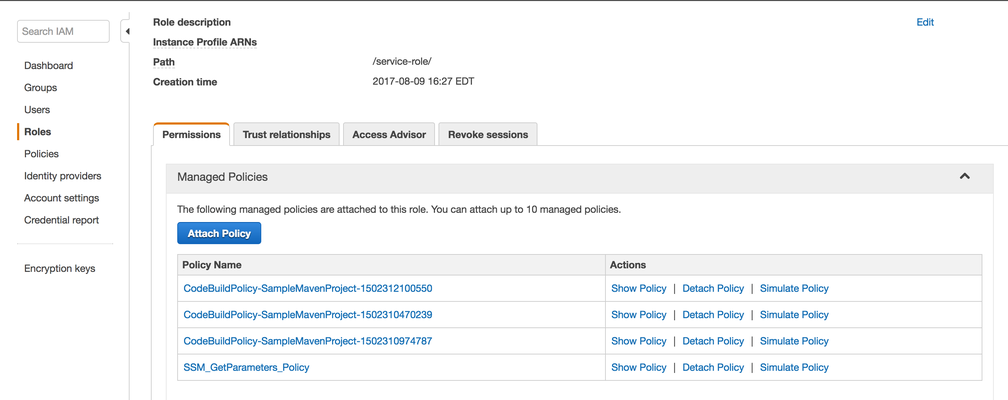
- Select the role and click Attach Policy.
- Find the Policy that was created, and then click Attach Policy.
The policy is attached as part of the role. This provides access to retrieve values from the parameter store.
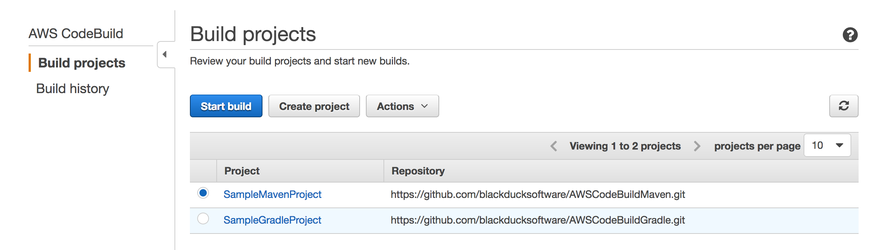
- Start the Build in AWS CodeBuild by selecting the project that you want ot build and then click Start build.
Viewing Black Duck Results
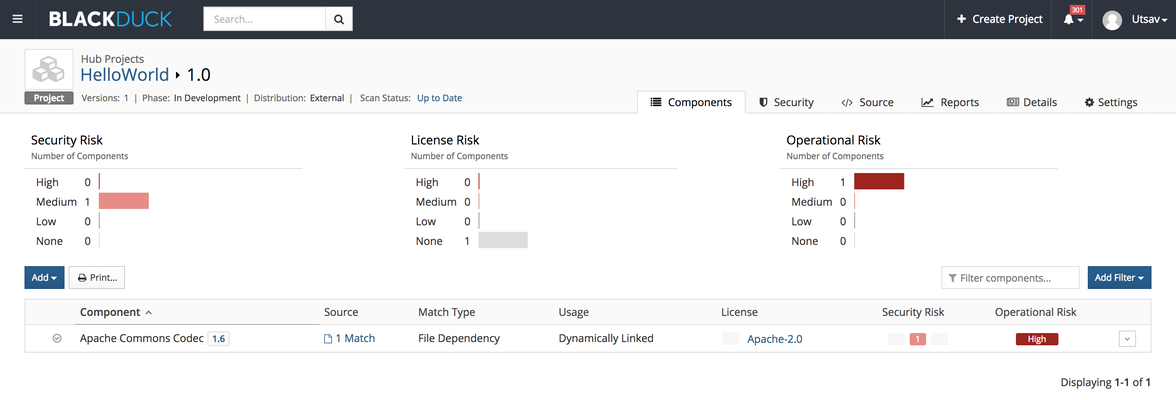
When you run a Black Duck scan from Synopsys Detect, take the following steps to view the results:
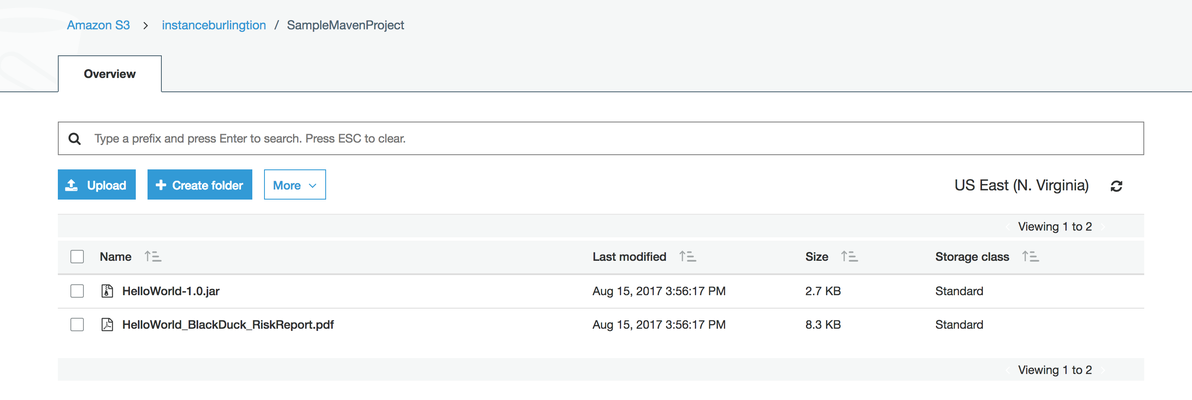
- Download and view the artifacts, which are pushed to the S3 bucket.
You can view the built artifact and the risk profile report in PDF format. - View the scan results in the Black Duck web interface.
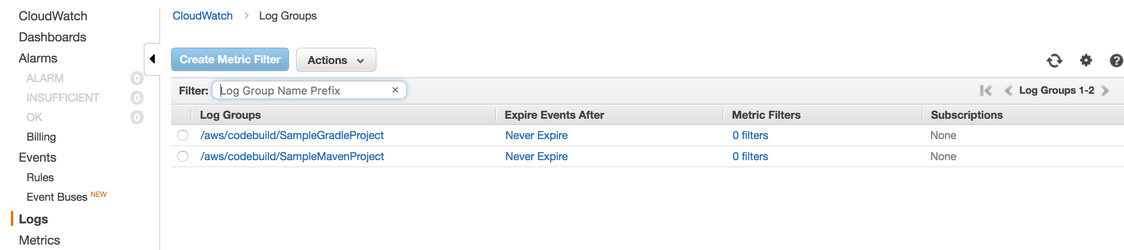
- To view the console logs, take the following steps:
- Login to https://console.aws.amazon.com
- Navigate to Services > Management Tools > CloudWatch > Logs.
- Select the corresponding project and check the latest log.
Other Configuration Options
The following options are alternative configuration options:
- For information about invoking AWS CodeBuild from Jenkins, refer to Invoking AWS CodeBuild from Jenkins.
- For information about using AWS command-line utilities rather than the AWS console, refer to Calling Synopsys Detect from AWS CodeBuild using the AWS command-line interface.
©2020 Synopsys, Inc. All Rights Reserved