Table of Contents
| Table of Contents | ||
|---|---|---|
|
...
Introduction Cloud Platform
In Google Cloud Platform, you can invoke Synopsys Detect in the following ways:
- In Google Cloud Build as a Custom Build Step, to scan with Black Duck and (optionally) perform an attestation for Binary Authorization.
- From other CI systems that run on Google Cloud.
...
Synopsys Detect sends scan data to Black Duck, which processes and displays scan results. For Synopsys Detect to connect to Black Duck, it must authenticate by using API tokens. To maximize security, Synopsys recommends that you use Google's Key Management Service to securely store your API Token. Click here for instructions about adding credentials to Google Cloud's Key Management Service.
...
In the build specification YAML file example, the $PROJECT_ID is not used in the kmsKeyName field because you must provide a hard-coded value.
Note: If your instance of Black Duck uses a self-signed certificate, ensure that you include the --blackduck.trust.cert argument in the args section of the YAML/JSON file that invokes the Cloud Build scanner. This allows the scanner to connect to a Black Duck instance whose certificate is not signed by a trusted third party. Refer to the build spec file example.
Caution: Build errors might occur when the --detect.tools argument and value are not included in the list of arguments.
...
As an alternative to invoking Google Cloud Build with a build-management system such as Jenkins, you can invoke the build process with Google Container Registry's build triggers. You can easily create a build trigger that instructs Google Cloud Build to automatically build your image whenever changes are pushed to the build source from any repository, including a cloud storage bucket. Click here for documentation about Google's Build Trigger functionality.
Note: To use Build Triggers, your repository must contain build configuration information in a cloudbuild.yaml file.
Submitting a build request using gcloud and verifying the results
...
| Code Block |
|---|
gcloud builds submit --config cloudbuild.yaml . |
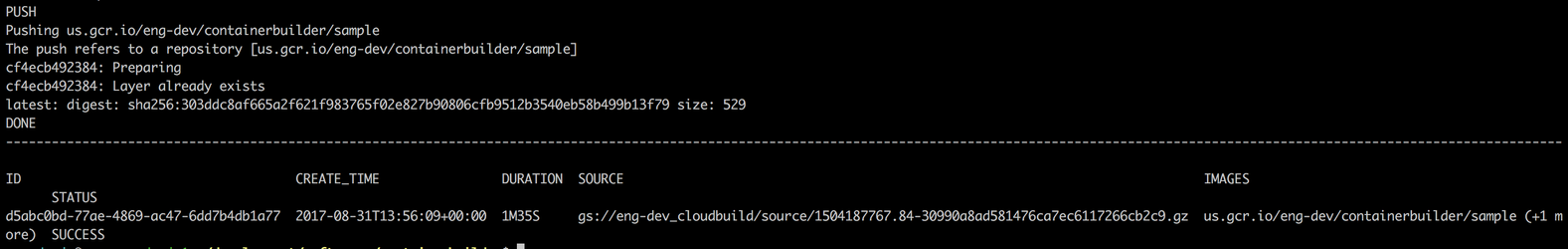
In this example, cloudbuild.yaml is the build configuration file. You must run this command from the source code home directory where the build specification file lives. After a successful run, a message displays, which is similar to the following example:
You should now be able to see the scan results in Black Duck.
...
| Code Block | ||||
|---|---|---|---|---|
| ||||
- name: 'gcr.io/cloud-builders/docker'
args: ['pull', '${_IMAGE_NAME}']
- name: 'gcr.io/cloud-builders/docker'
args: ['save', '-o', './${_IMAGE_NAME}.tar', 'gcr.io/$PROJECT_ID/${_IMAGE_NAME}']
- name: 'gcr.io/cloud-marketplace/blackduck-public/synopsys-cloudbuild-scanner'
secretEnv: [ 'BD_TOKEN' ]
args:
- '--blackduck.url'
- '<<Black Duck URL>>'
- '--blackduck.api.token'
- '$$BD_TOKEN'
- '--blackduck.trust.cert'
- 'true'
- '--detect.project.name'
- '${_IMAGE_NAME}'
- '--detect.project.version.name'
- 'container-tar'
- '--detect.tools' # List of Scanners to Run
- 'SIGNATURE_SCAN,BINARY_SCAN'
- '--detect.source.path' # Target for Signature Scan
- './${_IMAGE_NAME}.tar'
- '--detect.binary.scan.file.path'
- './${_IMAGE_NAME}.tar' # Target for Binary Scan
- '--detect.policy.check.fail.on.severities'
- 'BLOCKER'
substitutions:
_IMAGE_NAME: ducky-crm-cb
secrets:
- kmsKeyName: projects/[PROJECT-ID]/locations/global/keyRings/[KEYRING-NAME]/cryptoKeys/[KEY-NAME]
secretEnv:
BD_TOKEN: <base64-encoded encrypted Black Duck Token> |
Adding Synopsys credentials to Google Cloud Key Management Service (KMS)
Click here for instructions.
...